45467members
3048online
156647posts
Answers to the most common questions about the processor vulnerabilities and attack scenarios Meltdown and Spectre.
| Name | CVE-Nr. | Intel | AMD | ARM * | IBM Power |
| Spectre, Var. 1 (Bounds Check Bypass) | CVE-2017-5753 | ✓ | ✓ | ✓ | ✓ |
| Spectre, Var. 2 (Branch Target Injection) | CVE-2017-5715 | ✓ | - | ✓ | ✓ |
| Meltdown (Rogue Data Cache Load) | CVE-2017-5754 | ✓ | - | - | - |
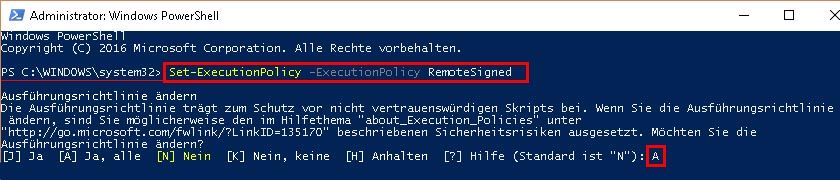

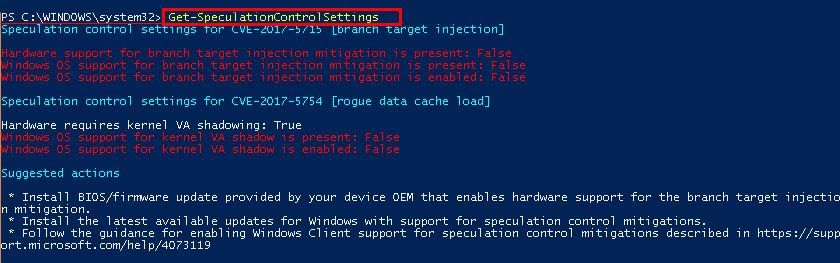
The information in this article refers to:
Review Date: 2020-07-01



